This sample Organizational Security Research Paper is published for educational and informational purposes only. Free research papers are not written by our writers, they are contributed by users, so we are not responsible for the content of this free sample paper. If you want to buy a high quality research paper on any topic at affordable price please use custom research paper writing services.
This research-paper explores the gap between organizational processes and security design. It starts with a presentation stressing the need for improved security in the corporation. Organizational processes such as work design, creativity, innovation, culture, learning, and change are considered in organizational design. The way the organization is designed and coordinated leads to the ability to reach its goals. Many factors influence the behavior and performance of the organization including the context, purpose, people, and structure as they interface with the core transformation and management support processes to set the organization’s performance level.
Most everything of tangible value in today’s society (and many intangibles as well) is stored in digital form somewhere. Without the knowledge to defend our digital assets, we are lost, and our potential loss grows larger everyday as we pour the contents of our lives into databases, PDAs, personal computers, and Web servers through routers, hubs, switches, cell phones, gateways, copper, coax, and the air itself. The need for security has existed since introducing the first computer. The paradigm has shifted in recent years, though, from terminal server mainframe systems, to client/server systems, to the widely distributed Internet (Wylder, 2004).
Although security is important, it has not always been critical to a company’s success. With a mainframe system, the firm protected their systems from resource abuse such as authorized users hogging resources or unauthorized users gaining access and using spare resources. Such abuse was damaging because system resources were costly in the early days of mainframes. As technology developed and the cost of system resources decreased, this issue became less important. Remote access to systems outside a company’s network was almost nonexistent. Moreover, only the underground community had the knowledge and tools needed to compromise a mainframe system.
Client/server technology developments led to a myriad of new security problems. Processor utilization was not a priority, but access to networks, systems, and files grew in importance. Access control became a priority as sensitive information such as human resources and payroll was being stored on public file servers. Companies did not want such data to be public knowledge, even to their employees, so new technologies such as granular access control, single sign-on, and data encryption were developed. As always, methods of circumventing and exploiting these new applications and security products quickly arose. During the client/server era, access into the corporate network was usually through a few dial-up accounts. This did open some security holes, but the risk to these accounts could be easily mitigated with procedures such as dial back and access lists. Branch offices communicated with one another over dedicated leased lines.
Then came the Internet—the open access worldwide network—and everything changed. The growth of e-mail and the World Wide Web soon led companies to provide Internet access to their employees. Developing an e-business initiative for your company became critical to stay competitive in the changing marketplace. With the rising use of the Internet, information including security information became accessible to the general public. Because the Internet is a public network, anyone on the Net can see other systems on it. As use of the Internet grew, companies started to allow more access to information and networks over the Internet. This approach, although beneficial for business, was inviting to attackers.
Recent events have led information security to become a significant focus in the way an organization conducts its business. Most businesses today have at least a rudimentary security program in place, and many programs are developing and growing in maturity. As these programs have grown, so has the need to move beyond the view that security is just a technical issue. Security today should be combined with the fabric of a business. In doing so, information security programs need to move from tactical implementations of technology to strategic partners in business (Wylder, 2004) Although companies were committed to developing a comprehensive information security program, they may not have integrated them into the framework of their businesses.
The Case For Information Security Scrutiny
Data in an information technology (IT) system is at risk from various sources—user errors and malicious and non-malicious attacks. Accidents can occur, and attackers can gain access to the system and can disrupt services, make systems useless, or change, delete, or steal information. Some companies have taken an enlightened view of security. They believe that, to be successful, they must show their customers that security and protecting information assets are a core business function. Security by design means that it is not an afterthought in the design process; instead, it is one of the requirements that designers use when starting a project. Secure in deployment means that products will be shipped and ready to use in a way that will not compromise the security of the customer or other products.
In the broadest definition, an information security program is a plan to mitigate risks associated with the processing of information. The security profession (Bensen, 2006) has defined the basics of security as three elements:
- Confidentiality. Confidentiality is preventing unauthorized use or disclosure of information. The system contains information that calls for protection from unauthorized disclosure. Examples include timed dissemination information (e.g., interim financial statements, personal information, and proprietary business information). Privacy is a closely related topic that has lately been getting more visibility.
- Integrity. Integrity is ensuring that information is accurate and complete and that it has not been modified by unauthorized users or processes. The system contains information that must be protected from unauthorized, unanticipated, or unintentional modification. Examples include survey reports, economic indicators, or financial transactions systems.
- Availability. Availability is ensuring that users have timely and reliable access to their information assets. The system contains information or provides services that must be available on a timely basis to meet mission requirements or to avoid substantial losses. Examples include online accessibility of business records, systems critical to safety, life support, and hurricane forecasting.
These three elements are the basics around which all security programs are developed. The three concepts are linked together in information protection. The idea that information is an asset that calls for protection, just like other asset of the business, is basic to understanding these concepts.
Ernst and Young Computer Security Institute conducts an annual study on Global Information Security. In Ersnt and Young’s 2002 study, 90% of respondents (large corporations and government agencies) detected computer security breaches; 70% reported a variety of serious computer security breaches except the most common ones of computer viruses, laptop theft, or employee “Net abuse”; 80% acknowledged financial losses caused by computer breaches; and 44% were willing and able to quantify their financial losses. The losses from these 223 respondents totaled $455,848,000; the most serious financial losses occurred through theft of proprietary information (26 respondents reported $170,827,000) and financial fraud (25 respondents reported $115,753,000). Progressing over the previous 5 years, more respondents (74%) cited their Internet connection as a frequent point of attack than those who cited their internal systems as a frequent point of attack (33%).
According to Jacques (2007), by mid-2006, reports of security breaches in the United States were numbering between 8 and 10 a week. To date, almost 94 million records containing sensitive personal information have been involved in security breaches. Another author addresses supplier interfaces as firms move to partnering and extranets (Williams, 2006) by noting that some 55% of firms are leaving themselves vulnerable to attack by failing to ensure the security credentials of third-party suppliers.
Other factors dealing with the loss of customer data (PGP Analyst Report, 2006) documents the high costs that result when companies lose customer data. Lost or stolen customer information cost surveyed companies as much as $22 million. The average cost for each lost customer record was $186. Incremental expenditures averaged $1.4 million for each incident. When a regulatory breach occurs, organizations must notify all affected customers, try to reduce downstream brand consequences, and put solutions in place to prevent a recurrence. Despite these consequences, new breaches are reported every week. Though security best practices dictate preventive technical solutions, most companies have not yet put such protections in place.
The 2004 Ernst and Young Global Information Security Survey found that, although company leaders are increasingly aware of the risks posed to their information security by people in their organizations, they are not acting on this knowledge. More than 70% of the 1,233 organizations—representing some of the leading companies in 51 countries—failed to list training and raising employee awareness of information security issues as a top initiative. (Ernst and Young, 2004)
As organizations move toward increasingly decentralized business models through outsourcing and other external partnerships, it becomes ever more difficult for them to retain control over the security of their information and for senior management to comprehend the risk to which they are exposed. The Ernst and Young surveys suggest that organizations continue to remain focused on external threats such as viruses, while internal threats are consistently understressed. Companies will readily commit to technology purchases such as firewalls and virus protection but are hesitant to assign priority to human capital.
Companies that are expanding into new markets and that are deploying operations in rapidly emerging economies face exponentially greater business risk including risk to vital corporate and customer information. Today’s huge opportunity can quickly become tomorrow’s nightmare—if the nightmare involves loss or corruption of company information, theft of trade secrets, exposure of customer information, or infiltration of systems (Global Information Survey, 2006).
Organization Processes And Security Considerations
Understanding and managing organizational processes such as work design, redesign, creativity, innovation, culture, learning, and change seems to absorb a significant time and energy in today’s business environment. Some managers argue that in reality their job almost entirely consists of managing change (Shani & Lau, 2005). Change comes about in many ways. The research-paper introduction described the changing face of information commerce among organizations based on introducing information communication technologies. These technologies have changed the way we work; they have altered the cultures within our firms.
The way the organization is designed and coordinated has major effect on the organization’s ability to reach its goals. Many factors influence the behavior and performance of the organization. These elements, as shown in Figure 49.1, can be grouped into six categories: the context, purpose, people, structure interface with the core transformation processes, and management support processes to set the organization’s performance level. All factors are affected by security.
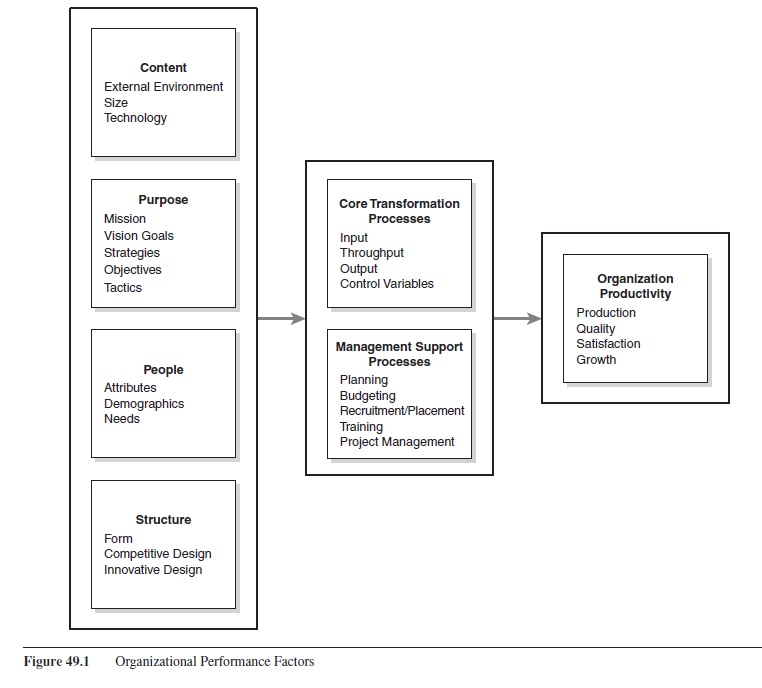 Figure 49.1 Organizational Performance Factors
Figure 49.1 Organizational Performance Factors
These factors, given that their security is properly addressed, lead to the ongoing success of the organization. Figure 49.2 shows those parts of the categories that are most affected by security considerations.
Most organizational knowledge is stored in digital form “somewhere” in the vast array of corporate data base systems. Beyond these formal corporate mechanisms are data stored in a wide variety of places and media. A company often has data stored on the workstations of all workers in and beyond the boundaries of the company. Work group and collaboration teams have data stored on local and virtual networks. Communication occurs in a wide variety of modes such as e-mail, messaging, voice mail, the telephone, and direct contact. Most of these data sources can also be saved in digital form—the company’s digital assets.
Context
Context refers to the entire organization including size, technology, and environment. Contextual dimensions affect the other categories such as structure, work processes, and ultimately, organization performance. The environment has a two-tier perspective: the task environment and the global environment. The task environment consists of the firm’s immediate relevant environment such as all customers, suppliers (of labor, knowledge, information, money, materials, etc.), markets, competitors, regulators, and associations that are relevant to the business’ current services and products. The global environment includes all the other possible environmental factors in which the organization functions such as political, educational, economy, demographic characteristics, societal structure, laws, and the many global impacts of doing business today.
Technology tools are the instruments, models, techniques, and processes that transform and support the business products and service. These tools are embedded in all business levels. They not only are part of the business, but they also emanate externally through social networks, the customer, and supply-chain interfaces to the outside world.
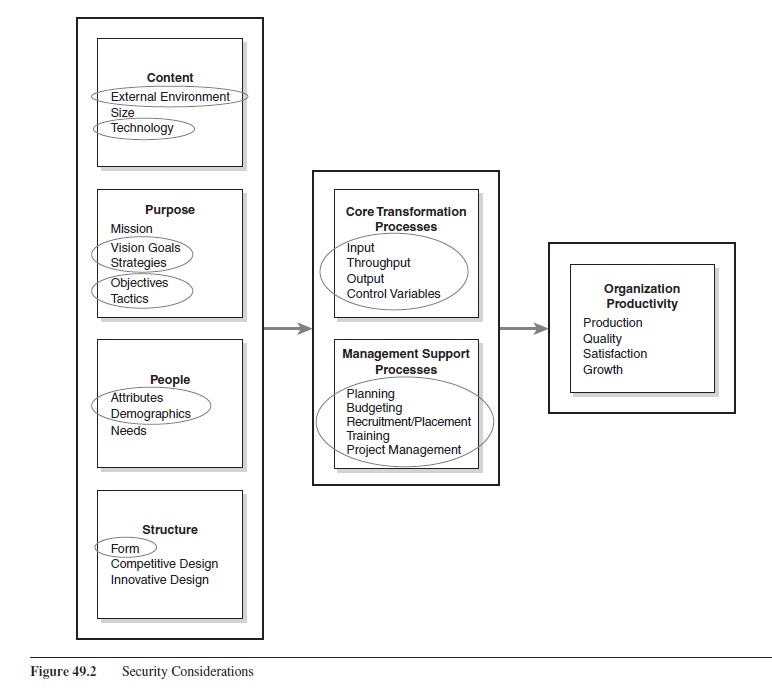 Figure 49.2 Security Considerations
Figure 49.2 Security Considerations
The Internet was introduced earlier in the research-paper; its opportunities are almost unlimited and challenging from a company perspective. Most of the primary tasks of doing business across the network have been addressed. But commerce and communication through the Internet continues to be a major security threat. Viruses and other external threats have and continue to shut down entire systems of electronic communication in and among organizations, records in databases are compromised, and private, delicate communications become not as private. The global environment and the choice of technology are intertwined.
Purpose
In defining purpose, we consider how the organization interprets the environment to develop statements of mission, vision, goals, strategies, objectives, and tactics. Although the firm’s mission may change slowly, important signals to employees are gained from formal communications from management about goals and priorities. Most business organizations have strategic plans that incorporate IT. Oftentimes, though, the IT part does not include a security plan. Instead, security is assumed to be in the IT infrastructure.
Strategically, executive management needs to be certain that all external and internal threats have been addressed through an information security plan and policy. The portal to the outside world is most often a series of defenses such as an outer firewall, an intermediate area in between to filter Internet traffic, and another firewall to control the liaisons between the company and the outside world. The next step is to verify that the operations in the organization have security measures in place. Decisions for grouping users and providing access rights and the ability to modify critical data are most often delegated to a security specialist. This specialist most likely does not view the workings of the organization in a macro sense, and he or she most likely is not vested with the authority or knowledge to align the corporate structure with the security structure.
People
Organizations have members with diverse attributes, demographic characteristics, and needs. Attributes include knowledge, skills, abilities, learning styles, and problem-solving styles. In many organizations, the collective knowledge sharing and learning becomes an organizational capability that is difficult for other companies to duplicate. Demographic characteristics are also important in building capabilities and improving organizational performance. Moreover, if organizations are to thrive, they must address employee needs, so employee satisfaction is potentially as important as the satisfaction of other stakeholders.
As companies are confronted with global competition, ecommerce, industry consolidation, new partnerships and alliances, and the like, there is a higher need for more internal and external coordination and collaboration. In this context, decisions are often made on a decentralized basis by teams that can use the best information at hand. One answer is a shift toward viewing the organization as “teams of teams” or the team-based organization (S. A. Mohrman, Cohen, & A. M. Mohrman, 1995).
The first line of defense is the individual worker. Most companies have in place a security system for the desktop and its interface to the corporate system either directly or through some form of local area network. The typical organization has PC-based workstations—most of which use Microsoft products. Microsoft and other end user software products provide the means to control the deployment of each workstation through user identification, rights, permissions, and access control lists. These controls are extended to the local and corporate environment in which the workstations are housed.
There is no substitute for employee awareness, the social aspect, and commitment to adhere to and to support the company’s security policy. Over two thirds of all security breaches occur from inside the organization. Attacker’s motives emanate from a variety of reasons. One reason may be employee resentment where an employee harbors feelings of mistreatment by the company and that the company owes them in some way. There are instances of the internal hacker or the just curious testing their skills by trying to gain unauthorized access not for revenge but just to experiment. Many workers have the ability to bypass the physical and logical controls put in place to protect the perimeter of the company’s network and have obtained credentials to access a significant part of its infrastructure. As no company can exist without employees, it is the inevitable reality that some individuals are potential security risks. People will always be susceptible to manipulation, but it is possible to combat this to an extent with proper training and awareness along with other security measures.
Employees are the most difficult part of security management to address and control. Security policies do not always follow the chain of command or the formal/informal systems of communication. There is, often, a lack of support or conflict over the enforcement and enactment of security policies. Sometimes the security manager will try to enforce policies for all without trying to temper enforcement with judgment. Enforcement to the security manager includes penalizing the people who break the rules. Other managers look at security policies the same way they look at all policies and weigh the punishment with the crime. Access control violations are compared to violations of accounting policy and the myriad of other rules that exist in the workplace today. Executive management has to weigh all types of policies with the other goals and objectives of the business. This is not too different from the security manager’s decisions about access controls and authorization. The security manager has to weigh the need to know against the want to know, where the line always calls for greater access to information than the former. The convergence of the executive manager and the security manager decisions is in the balancing of their goals and objectives. One way to improve communication between the executive team and the security area is security area is to link decisions to find common goals and objectives and then work on disagreements.
Organizations invest heavily in the latest firewalls, intrusion detection systems, and other advanced security technologies, yet losses from security incidents continue to grow each year (Gunther, 2004). The problem is not so much with security technology as it is with the lack of security awareness among users. All too often information security professionals have to deal with breaches caused by users opening an e-mail attachment with a virus that reproduces itself across the enterprise, forgetting to back up critical files, using weak passwords, losing laptops with confidential data, or being tricked into giving up their passwords through social engineering techniques. Security experts acknowledge that an organization’s first line of defense is the frontline employees who interact with customers, process their information, and pass it along to others in the delivery chain. Most discussions of security and privacy compliance mention that successful initiatives need sweeping cultural changes including changes in operational processes and behaviors.
Structure
The term structure has many meanings. Research studies on organizations have identified structural variables such as levels in the hierarchy, formalization (the written documentation, as in policies, procedures manuals, job descriptions, etc.), standardization (the extent to which activities must be performed in a uniform way), and centralization (at what decision levels). Form of structure refers to the method of grouping employees together into work units, departments, and the organization.
As the organization grows, differentiation of specialty units occurs, with managers appointed for each unit. Functional organizations tend to be efficient and work well when the business situation and outside environment are stable. Employees then take on increasingly complicated tasks and grow through special assignments and applications of their skills. On the negative side, people in functional organizations often develop parochial viewpoints, and interdepartmental cooperation can be poor. Department goals often differ, and decisions are often pushed up the hierarchy, slowing deliberations and blocking needed changes. As the company’s products and customers expand, other forms of structure may appear more attractive to top management.
With rising company size, product divisions or other self-contained units are often created to replace the functional organization. With greater diversification of products and greater diversification in customers and markets served, a company may choose to reorganize according to its major products. When this occurs, each product group gains discretion to design, produce, and distribute its products in ways that are consistent with the competitive environment. If the new product groups are organized in the same basic way (research and development [R&D], manufacturing, accounting, and marketing), it can be argued that nothing new has occurred. The product groups still appear functional, and people may behave in the same ways. If the structure and support processes change to stress multispecialty teams or other forms of teamwork, a truly new form might exist.
Security assumes several new dimensions when local area networks (LANs) or wide area network (WANs) are introduced. This second line of defense includes the tools provided by Microsoft for their workstations and LAN and the network security provisions provided by Cisco-level measures (Cisco Inc. being the primary provider of WAN and Internet hardware and software). As the workstations are connected to routers and switches, each interface can be individually controlled to allow access based on the user, the type of protocol being used, and the network or subnetwork of origin or destination. It is more difficult to compromise such measures.
There are three logical (and possibly physical) parts to the corporate network infrastructure—intranet, extranet, and internet. Each of these parts are separated/isolated/ protected by/from some form of firewall. The intranet is the secure layer where the internal operations of the company are conducted. The extranet is the less secure layer where the company conducts its commerce with its partners along the supply chain. The Internet is the unsecured environment where the company communicates with the business world and the general consumer.
With Internet use, information sometimes including security information becomes accessible to the public. Because the Internet is a public network, anyone on the Net could potentially see other systems. At first, this was not a major issue because sensitive information was not easily accessible. As use of the Internet grew, companies permitted access to information and networks over the Internet.
Core Transformation Process
The core transformation process is the conversion process turning inputs into output. Looking at it from a strictly technical systems view input combined with technology produces “throughput” or “product-in-becoming” (Taylor & Felten, 1993). Throughput is the state of the product at an earlier stage of development. Management and employees must apply technology and control variances so that the core transformation process is sound. Security is endemic in the core transformation process. At every stage, measures must be in place to insure that the customer orders are received; that the billing information is secured; and that communications with vendors for purchases, processing of the orders, and the distribution and collection are assured. The means to secure (authenticated) transaction has been addressed in many systems and is provided by software vendors and the communication industry. It is the responsibility of each company to insure that they have incorporated these features into their internal systems.
Management Support Processes
Form of structure alone is not enough to coordinate and meet the needs of a thriving enterprise. Companies invest considerable time and resources in setting up processes that support the typical core activities of new product development, sales, order fulfillment, and customer service. Management support processes vary with the enterprise but include planning, budgeting, quality management, recruitment, placement, training, project management, and other valued processes. Decisions to build staff support departments and processes usually follow strategy and core transformation decisions. That is, investment in management support is justified if the purpose, core transformation processes, and structure call for capabilities to meet requirements of the business and industry.
Before, companies often chose to centralize management support groups at the corporate level. Staff members were then deployed to provide support or needed corporate controls. Often, the reaction from lower management was negative, as staff personnel demanded time and resources in carrying out their roles in divisions and departments of the company. The staff members too often carried the corporate perspective of control to true service and support to managers and employees in the field. Today, the situation is much improved in most corporations because of two developments in organization design. First, corporations have experienced waves of downsizing as a strategic move and as a way to cut costs. Often, there are fewer, smaller corporate staff work units and service groups. A second development in organization design is physical location of staff groups. When service groups are located with operations groups, there is a greater sense of cooperation, teamwork, and identity with operations managers and work teams. Under distributed organization, divisions and departments are encouraged to develop support groups that are close to the real operations action. For example, rather than locate a corporatewide IT group at headquarters, in a multidivision firm, one division might have such a group to serve its own needs and to serve all other company divisions. When this idea is extended to other staff support groups, a situation emerges where divisions help each other and bring in new ideas, methods, and technologies to improve operations throughout the company.
Management may view their information systems infrastructure as an inevitable evil rather than as a critical business process (Cassidy, 1998). Many times, this is attributable to a lack of understanding and communication. Information systems are expensive assets for a company. Management must clearly understand their information systems environment to manage this asset as they would other business assets. The planning process will significantly improve the communication between management and information systems. Management hopes to gain a better understanding of their current systems and to identify potential risks and opportunities. Information systems will better understand the business direction and the role of technology.
The information systems direction must align with business drivers and must conform to boundary conditions imposed by the business environment. Boundary conditions may limit what can be done. Information is a valuable resource, and it is important to raise its value for the corporation. Planning and managing the information flow throughout the organization can reduce labor, data redundancy, and inconsistency besides raising the quality and accuracy of the information.
Developing systems that provide the business with a competitive advantage must be the focus rather than simply satisfying the wheel that squeaks the loudest. Some information systems managers are efficient in developing a strategic plan by taking their top computer technicians and outlining the technical architecture of the future. When these technicians finish their planning, they may have an ideal technical plan, but one that management may not totally understand let alone approve. These plans tend to accumulate dust on someone’s bookshelf and never affect the direction of information systems or the business. The plan must show management ideas, styles, and objectives. To be successful, the entire organization must support the information systems objectives.
As the business environment becomes more dynamic and volatile, the technology planning process must be more flexible and responsive. The planning process should not be too rigid or formal. It should provide the opportunity for many face-to-face meetings between the important participants. Structure for the process should provide well-defined forums for interaction rather than rigidly specified planning documents. Perhaps a better mechanism for delivering the work of planning teams is for the line manager to present the departmental IT plan periodically to other senior managers, the CIO, and to members of his own staff.
A Solutions Framework
Identifying Assets And Vulnerabilities To Known Threats
Assessing an organization’s security needs also includes finding out its vulnerabilities to known threats. This assessment entails recognizing the types of assets that an organization has, which will suggest the types of threats it needs to protect itself against. Figure 49.3 depicts a security strategy methodology (Bensen, 2006) entailing proactive and reactive strategies.
Identifying Likely Attack Methods, Tools, And Techniques
The first step is to find out the attacks that can be expected and ways of defending against these attacks. It is impossible to prepare against all attacks and, therefore, prepare for the most likely attacks that the organization can expect. It is always better to prevent or minimize attacks than it is to repair the damage after an attack has already occurred.
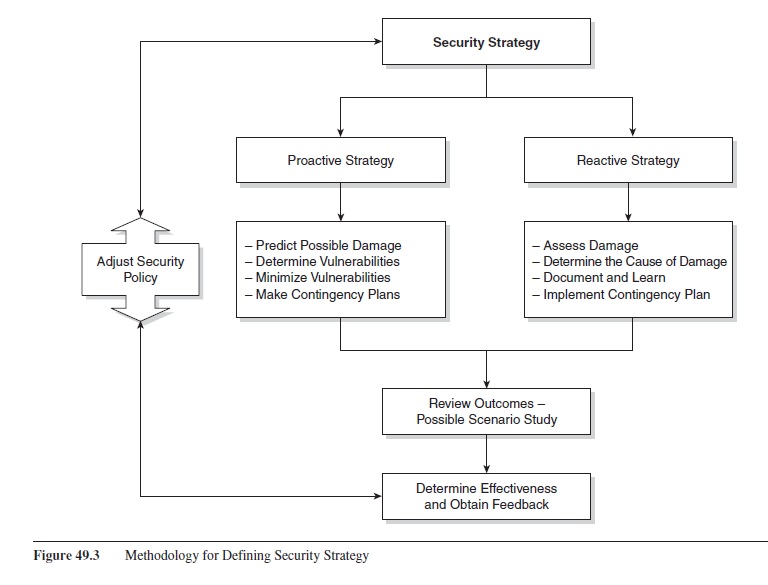 Figure 49.3 Methodology for Defining Security Strategy
Figure 49.3 Methodology for Defining Security Strategy
To reduce attacks, the various threats that cause risks to systems, the corresponding techniques that can be used to compromise security controls, and the vulnerabilities that exist in the security policies need to be understood. Understanding these three parts of attacks helps us to predict their occurrence, if not their timing or location. Predicting an attack is a matter of predicting its likelihood, which depends on understanding its various aspects. The various aspects of an attack can be shown in an equation: threats + motives + tools and techniques + vulnerabilities = attack.
Setting Proactive And Reactive Strategies
The proactive or preattack strategy consists of steps to address current security policy vulnerabilities and develop contingency plans. Assessing the damage that an attack will cause on a system and the weaknesses and vulnerabilities exploited during this attack helps in developing the proactive strategy.
The reactive strategy or postattack strategy helps security personnel to assess the damage caused by the attack, repair the damage or put into effect the contingency plan developed in the proactive strategy, document and learn from the experience, and get business functions running as soon as possible.
Reviewing The Outcomes And Possible Scenario Study
Reviewing the outcomes after the reactive and proactive strategies have been put into place is the next step. Creating scenarios for what-if alternatives to simulate attacks helps to assess where the various vulnerabilities exist and adjust security policies and controls. The scenarios provide information without having to perform live production system because the outcome could be disastrous. If possible, all attack scenarios should be physically tested and documented to find the best possible security policies and controls to be put into effect. Attacks such as natural disasters like floods and lightning cannot be tested, although a simulation will help. For example, simulated fire in the server room has resulted in all the servers being damaged and lost. This scenario can be useful for testing the responsiveness of administrators and security personnel and for ascertaining how long it will take to get the organization functional again. Testing and adjusting security policies and controls based on scenario examinations is an iterative process. It is never finished and should be evaluated and revised periodically so that improvements can be put into effect.
Contingency Planning
A contingency plan looks at alternatives that should be developed in case an attack penetrates the system and damages data or other assets with the result of halting normal business operations and hurting productivity. The plan is followed if the system cannot be restored in a timely way. Its ultimate goal is to maintain the availability, integrity, and confidentiality of data.
There should be a plan for each type of attack and threat. Each plan consists of steps to take if an attack breaks through the security policies. The contingency plan should address who must do what and where to keep the organization operating. This assumes that the current emergency response procedures and their effects have been evaluated—noting the extent to which they are adequate to limit damage and reduce the attack’s impact on the organization’s operations.
Conclusions And Future Directions
Security as a Competitive Edge
A properly implemented security infrastructure (Andres, 2004) can become a competitive advantage, providing protection to corporate assets that set the company except for its competitors. If a company’s main competitor is looking to launch e-business initiatives, the company with the stronger security infrastructure will be more successful. Why? First, the company with the weaker security infrastructure might be more reluctant to launch e-business projects because it is concerned with security and does not know how to protect itself adequately. Second, and more commonly, the weaker company will ignore the security aspect of online business and then wonder why it suffered a successful attack against its systems. This inattention could lead to the compromise of critical sensitive data—maybe customer credit cards or business bank account numbers—and the subsequent loss of customers. The company with the stronger security environment can more safely launch an online business initiative, knowing that its corporate security infrastructure is strong enough to protect it. If its systems do happen to be compromised, the business response plan in place should lower the damage.
Management Buy-In
Security programs should involve all aspects of the organization. Management support and organization buy-in are key to the success of a security infrastructure. A program works best when it is built around a framework of established policies, standards, and procedures. If put into effect properly, a security infrastructure will help curtail practices that seem to have become the norm in most organizations such as employees writing down passwords on notepaper and storing the notes under their keyboards or mouse pads. It can also stop social engineering and physical attacks such as fake help desk calls asking to reset passwords or dumpster diving. A comprehensive security program also must address business partners who create potential security breaches by improperly securing their own networks and systems, leaving them as backdoors into your network.
Recognition That Security Is Key to the Business
The inexorable drive of companies to lower costs and raise productivity has entailed raised reliance on the Internet. Information security is a pervasive concern for all companies, not simply those that rely to a varying extent on the Internet to conduct business. An accurate gauge (Raval, 2003) of losses resulting from IT security incidents needs to be established. Given the tight corporate budgets, IT managers, risk managers, and finance policy makers need reliable quantitative estimates on enterprise IT security.
Studies (e.g., Raval, 2003) have shown that IT can be a major source of productivity gains. The results are likely to be variable, depending on the specific IT investment at the firm level. Productivity improvements often arise from competitive pressures, which lead to process innovations, some of which involve deployment of IT. If IT investment is not for a business process innovation, chances are that little gain in productivity can be anticipated or will occur.
References:
- Andress, A. (2004). Surviving security: How to integrate people, process, and technology (2nd ed.). Baton Rouge, LA: CRC Press LLC.
- Belsis, P., & Kokolakis, S. (2005). Information systems security from a knowledge management perspective. Information Management & Computer Security, 13(3), 189-202.
- Bensen, C. (2006). Security strategies. Retrieved September 1, 2007, from http://www.microsoft.com/technet/archive/secu rity/bestprac/bpent/sec1/secstrat.mspx?mfr=true
- Brint Institute. (2007). Business technology management and knowledge management research network. Retrieved September 1, 2007, from http://www.brint.com
- Cassidy, A. (1998). A practical guide to information systems planning. Baton Rouge, LA: CRC Press LLC.
- Computerworld Inc. (2007). ITworld.com. Retrieved September 1, 2007, from http://www.itworld.com
- Davis, B. J. (2005). PREPARE: Seeking systemic solutions for technological crisis management. Knowledge and Process Management, 12(2), 123-131.
- Ernst and Young. (2002). Global information security survey 2002. Retrieved September 3, 2007, from http://www.esteem.co.uk/ products/security/Global_Information_Security Survey.pdf
- Ernst and Young. (2004). Global information security survey 2004. Retrieved from http://www.ey.com/global/download.nsf/ UK%20/Survey_-_Global_Information_Security_04/$file/ EY_GISS_97202004_EYG.pdf
- Ernst and Young LLP. (2006). Achieving success in a globalized world: Is your way secure? Global information security survey 2006. Retrieved September 1, 2007, from http:// www.ey.com/global/content.nsf/International/Assurance_ &_Advisory_-_Technology_and_Security_Risk_-_Global_ Information_Security_Survey_2006
- Garg, A., Curtis, J., & Halper, H. (2003). Quantifying the financial impact of IT security breaches. Information Management & Computer Security, 11(2), 74-83.
- Gordon, L. A., Loeb, M. P., Lucyshyn, W., & Richardson, R. (2006). CSI/FBI computer crime and security survey. GoCSI. com. Retrieved September 3, 2007, from http://www.cse .msu.edu/~cse429/readings06/FBI2006.pdf
- Guenther, M. (2004, June). Security/privacy compliance: Culture change, EDPACS: The EDP Audit, Control, and Security Newsletter. 31(12), 19-25.
- Hong, K. S., Chi, Y. P., Cho, L. R., & Tang, J.-H. (2003). An integrated systems theory of information security management. Information Management & Computer Security, 11(5), 243-248.
- Jacques, R. (2006, December 14). Global firms reach compliance breaking point. Retrieved September 1, 2007, from http:// www.vnunet.com/vnunet/news/2171043/global-firms-reach-compliance
- Kokolakis, S. A., Demopoulos, A. J., & Kiountouzis, E. A. (2000). The use of business process modeling in information systems security analysis and design. Information Management & Computer Security, 8(3), 107-116.
- Kwok, L.-F., & Longley, D. (1999). Information security management and modeling. Information Management & Computer Security, 7(1), 30-40.
- Mohrman, S. A,. Cohen, S. G., & Mohrman, A. M., Jr. (1995). Designing team-based organizations: New forms for knowledge work. San Francisco: Jossey-Bass.
- Peltie, T. R. (2004, March/April). Developing an enterprise-wide policy structure. Information Security Management.
- Peter, R. J. (2005). Trim: Managing computer security issues— Preventing and limiting future threats and disasters. Disaster Prevention and Management, 14(4), 493-505.
- PGP Corporation. (2006, October 1). Vontu, Inc. Palo Alto, CA.
- Raval, V. (2003, Spring). Security, society, and skepticism. The Executive’s Journal, 19(3), 43-48.
- Raval, V. (2003, Fall). Productivity and information technology. Information Strategy: The Executive’s Journal, 20(1), 37-40.
- Shani, A. B., & Lau, J. (2005). Behavior in organizations. New York: McGraw-Hill/Irwin.
- Taylor, J. C., & Felten, D. P. (1993). Performance by design: Sociotechnical systems in North America. Englewood Cliffs, NJ: Prentice Hall.
- Tech Target. (2007, September 1). Information security: Covering today’s security topics. Retrieved September 1, 2007, from http://searchsecurity.techtarget.com
- Williams, L. (2006, November 16). Third-party security risks overlooked. Computing. Retrieved September 1, 2007, from http://www.vnunet.com/computing/news/2168718/third-party-security-risks
- com. (2007). Network security articles for windows server 2003, 2008 & Vista. Retrieved September 1, 2007, from http://www.windowsecurity.com/
- Wylder, J. (2004). Strategic information security. Boca Raton, FL: Auerbach Publications.
See also:
Free research papers are not written to satisfy your specific instructions. You can use our professional writing services to order a custom research paper on any topic and get your high quality paper at affordable price.





